Cisco VPN client is not supported for Windows 10. In order to make it work you have to extract the MSI file, install a Dell Sonicwall VPN client, install the MSI, and then make a few registry tweaks to make the software recognize the VPN adapter that was created. Please contact your IT Department for Windows 10 compatible versions. AnyConnect Plus/Apex licensing and Cisco head-end hardware is required. The application is not permitted for use with legacy licensing (Essentials or Premium PLUS Mobile). AnyConnect may not be used with non-Cisco hardware under any circumstances.
- Anyconnect Install On Windows 10
- R/Intune - Has Anyone Figured Out How To Deploy Cisco VPN ...
- DeployAnyConnect - Cisco
- Cisco Anyconnect Intune Windows 10 Free
- Configure ASA AnyConnect VPN With Microsoft Azure MFA ... - Cisco
- Cisco Anyconnect Intune Windows
- Intune Vpn Profile Cisco Anyconnect Windows 10
Introduction
This document describes how to configure Security Assertion Markup Language (SAML) with a focus on Adaptive Security Appliance (ASA) AnyConnect through Microsoft Azure MFA.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Basic knowledge of RA VPN configuration on ASA.
- Basic knowledge of SAML and Microsoft Azure.
- AnyConnect Licenses enabled (APEX or VPN-Only).
Components Used
The information in this document is based on these software and hardware versions:
- A Microsoft Azure AD subscription.
- Cisco ASA 9.7+ and Anyconnect 4.6+
- Working AnyConnect VPN profile
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background Information
SAML is an XML-based framework for exchanging authentication and authorization data between security domains. It creates a circle of trust between the user, a Service Provider (SP), and an Identity Provider (IdP) which allows the user to sign in a single time for multiple services. Microsoft Azure MFA seamlessly integrates with Cisco ASA VPN appliance to provide additional security for the Cisco AnyConnect VPN logins.
SAML Components
Metadata: It is an XML based document that ensures a secure transaction between an IdP and an SP. It allows the IdP and SP to negotiate agreements.
Roles supported by the devices (IdP, SP)
A device may support more than one role and could contain values for both an SP and an IdP. Under the EntityDescriptor field is an IDPSSODescriptor if the information contained is for a Single Sign-On IdP or a SPSSODescriptor if the information contained is for a Single Sign-On SP. This is important since the correct values must be taken from the appropriate sections in order to set up SAML successfully.
Entity ID: This field is a unique identifier for an SP or an IdP. A single device might have several services and can use different Entity IDs to differentiate them. For example, ASA has different Entity IDs for different tunnel-groups that need to be authenticated. An IdP authenticating each tunnel-group has a separate Entity ID entries for each tunnel-group in order to accurately identify those services.
ASA can support multiple IdPs and has a separate entity ID for each IdP to differentiate them. If either side receives a message from a device that does not contain an entity ID that has been previously configured, the device likely drops this message, and SAML authentication fails. The Entity ID can be found within the EntityDescriptor field beside entityID.
Service URLs: These define the URL to a SAML service provided by the SP or IdP. For IdPs, this is most commonly the Single Logout Service and Single Sign-On Service. For SPs, this is commonly the Assertion Consumer Service and the Single Logout Service.
The Single Sign-On Service URL found in the IdP metadata is used by the SP to redirect the user to the IdP for authentication. If this value is incorrectly configured, the IdP does not receive or is unable to successfully process the Authentication request sent by the SP.
The Assertion Consumer Service URL found in the SP metadata is used by the IdP to redirect the user back to the SP and provide information about the user's authentication attempt. If this is configured incorrectly, the SP does not receive the assertion (the response) or is unable to successfully process it.
The Single Logout Service URL can be found on both the SP and the IdP. It is used to facilitate logging out of all SSO services from the SP and is optional on the ASA. When the SLO service URL from the IdP metadata is configured on the SP, when the user logs out of the service on the SP, the SP sends the request to the IdP. Once the IdP has successfully logged the user out of the services, it redirects the user back to the SP using the SLO service URL found within the SP’s metadata.
SAML Bindings for Service URLs: Bindings are the method the SP uses to uses to transfer information to the IdP and vice versa for services. This includes HTTP Redirect, HTTP POST, and Artifact. Each method has a different way of transferring data. The binding method supported by the service is included within the definition of that services. For example: SingleSignOnService Binding='urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect' Location='https://saml.example.com/simplesaml/saml2/idp/SSOService.php'/ >. The ASA does not support the Artifact binding. ASA always uses the HTTP Redirect method for SAML authentication requests, so it is important to choose the SSO Service URL that uses the HTTP Redirect binding so that the IdP expects this.
Certificates for Signature and Encryption Operations
To provide confidentiality and integrity for the messages sent between the SP and the IdP, SAML includes the ability to encrypt and sign the data. The certificate used to encrypt and/or sign the data can be included within the metadata so that the receiving end can verify the SAML message and ensure that it comes from the expected source. The certificates used for signing and encryption can be found within the metadata under KeyDescriptor use='signing' and KeyDescriptor use='encryption', respectfully, then X509Certificate. The ASA does not support encrypting SAML messages.
Network Diagram
Configure
Add Cisco AnyConnect from the Microsoft App Gallery
Step 1. Log in to Azure Portal and select Azure Active Directory.
Step 2. As shown in this image, select Enterprise Applications.
Step 3. Now select New Application, as shown in this image.
Step 4. In the Add from the gallery section, type AnyConnect in the search box, select Cisco AnyConnect from the results panel, and then add the app.
Step 5. Select the Single Sign-on menu item, as shown in this image.
Step 6. Select SAML, as shown in the image.
Step 7. Edit Section 1 with these details.
Step 8. In the SAML Signing Certificate section, select Download to download the certificate file and save it on your computer.
Step 9. Note this, it is required for ASA configuration.
- Azure AD Identifier - This is the saml idp in our VPN configuration.
- Login URL - This is the URL sign-in.
- Logout URL - This is the URL sign-out.
Assign Azure AD User to the App
Anyconnect Install On Windows 10
In this section, Test1 is enabled to use Azure single sign-on, as you grant access to the Cisco AnyConnect app.
Step 1. In the app's overview page, select Users and groups and then Add user.
Step 2. Select Users and groups in the Add Assignment dialog.
Step 3. In the Add Assignment dialog, click the Assign button.
Configure ASA for SAML via CLI
Step 1. Create a Trustpoint and import our SAML cert.
Step 2. These commands provision your SAML IdP.
Step 3. Apply SAML Authentication to a VPN Tunnel Configuration.
Note: If you make changes to the IdP config you need to remove the saml identity-provider config from your Tunnel Group and re-apply it for the changes to become effective.
Verify
Test AnyConnect with SAML Auth
Step 1. Connect to your VPN URL and input your login Azure AD details.
Step 2. Approve sign-in request.
Step 3. AnyConnect is Connected.
Common Issues
Entity ID Mismatch
Debug Example:
[SAML] consume_assertion: The identifier of a provider is unknown to #LassoServer. In order to register a provider in a #LassoServer object, you must use the methods lasso_server_add_provider() or lasso_server_add_provider_from_buffer().
Problem: Generally means that saml idp [entityID] command under the ASA's webvpn configuration does not match the IdP Entity ID found in the IdP’s metadata.
Solution: Check the entity ID of the IdP’s metadata file and change the saml idp [entity id] command to match this.
Time Mismatch
Debug Example:
[SAML] NotBefore:2017-09-05T23:59:01.896Z NotOnOrAfter:2017-09-06T00:59:01.896Z timeout: 0
[SAML] consume_assertion: assertion is expired or not valid
Problem 1. ASA time not synced with IdP’s time.
Solution 1. Configure ASA with the same NTP server used by IdP.
Problem 2. The assertion is not valid between the specified time.
Solution 2. Modify the timeout value configured on the ASA.
Wrong IdP Signing Certificate Used
Debug Example:
[Lasso] func=xmlSecOpenSSLEvpSignatureVerify:file=signatures.c:line=493:obj=rsa-sha1:subj=EVP_VerifyFinal:error=18:data do not match:signature do not match
[SAML] consume_assertion: The profile cannot verify a signature on the message
Problem: ASA not able to verify the message signed by the IdP or there is no signature for the ASA to verify.
Solution: Check the IdP signing certificate installed on the ASA to make sure it matches what is sent by the IdP. If this is confirmed, make sure that the signature is included in the SAML response.
Invalid Assertion Audience
Debug Example:
[SAML] consume_assertion: assertion audience is invalid
Problem: IdP is defining the incorrect audience.
Solution: Correct the Audience configuration on the IdP. It should match the ASA’s Entity ID.
Wrong URL for Assertion Consumer Service
Example Debug: Unable to receive any debugs after the initial authentication request is sent. The user is able to enter credentials at IdP but IdP does not redirect to ASA.
R/Intune - Has Anyone Figured Out How To Deploy Cisco VPN ...
Problem: IdP is configured for the wrong Assertion Consumer Service URL.
Solution(s): Check base URL in configuration and make sure it is correct. Check ASA metadata with show to make sure that the Assertion Consumer Service URL is correct. In order to test it, browse it, If both are correct on the ASA, check the IdP to make sure that the URL is correct.
SAML Configuration Changes Not Taking Effect
Example: After a single sign-on URL is modified or changed, the SP certificate, SAML still does not work and sends previous configurations.
Problem: ASA needs to regenerate it's metadata when there is a configuration change that affects it. It does not do this automatically.
Solution: After making changes, under the affected tunnel-group remove and re-apply the saml idp [entity-id] command.
Troubleshoot
Most SAML troubleshoots involve a misconfiguration that can be found when the SAML configuration is checked or debugs are run. debug webvpn saml 255 can be used to troubleshoot most issues, however in scenarios where this debug does not provide useful information, additional debugs can be run:
Related Information
-->Note
Intune may support more settings than the settings listed in this article. Not all settings are documented, and won’t be documented. To see the settings you can configure, create a device configuration profile, and select Settings Catalog. For more information, see Settings catalog.
You can add and configure VPN connections for devices using Microsoft Intune. This article describes some of the settings and features you can configure when creating virtual private networks (VPNs). These VPN settings are used in device configuration profiles, and then pushed or deployed to devices.
As part of your mobile device management (MDM) solution, use these settings to allow or disable features, including using a specific VPN vendor, enabling always on, using DNS, adding a proxy, and more.
These settings apply to devices running:
- Windows 10
- Windows Holographic for Business
Before you begin

Deploy your VPN app, and create a Windows 10 VPN device configuration profile. The available settings depend on the VPN client you choose. Some settings are only available for specific VPN clients.
These settings use the VPNv2 CSP.
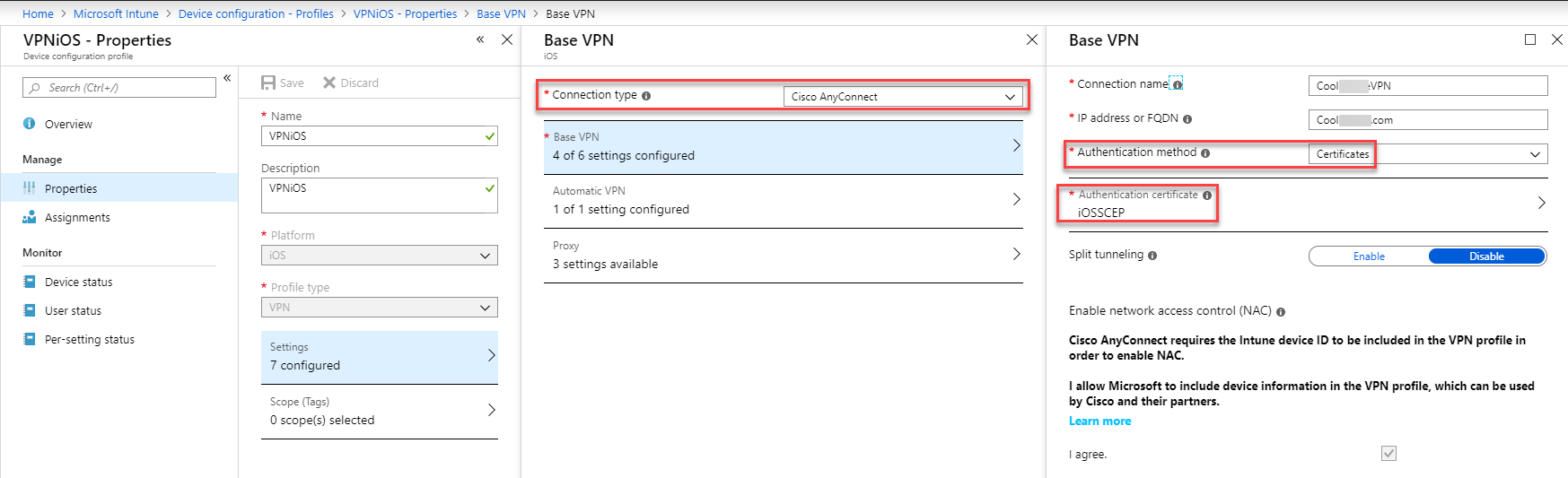
Base VPN
Connection name: Enter a name for this connection. End users see this name when they browse their device for the list of available VPN connections.
Servers: Add one or more VPN servers that devices connect to. When you add a server, you enter the following information:
- Description: Enter a descriptive name for the server, such as Contoso VPN server.
- IP address or FQDN: Enter the IP address or fully qualified domain name (FQDN) of the VPN server that devices connect to, such as 192.168.1.1 or vpn.contoso.com.
- Default server: Enables this server as the default server that devices use to establish the connection. Set only one server as the default.
- Import: Browse to a comma-separated file that includes a list of servers in the format: description, IP address or FQDN, Default server. Choose OK to import these servers into the Servers list.
- Export: Exports the list of servers to a comma-separated-values (csv) file.
Register IP addresses with internal DNS: Select Enable to configure the Windows 10 VPN profile to dynamically register the IP addresses assigned to the VPN interface with the internal DNS. Select Disable to not dynamically register the IP addresses.
Connection type: Select the VPN connection type from the following list of vendors:
- Cisco AnyConnect
- Pulse Secure
- F5 Access
- SonicWall Mobile Connect
- Check Point Capsule VPN
- Citrix
- Palo Alto Networks GlobalProtect
- Automatic
- IKEv2
- L2TP
- PPTP
When you choose a VPN connection type, you may also be asked for the following settings:
Always On: Enable automatically connects to the VPN connection when the following events happen:
- Users sign into their devices
- The network on the device changes
- The screen on the device turns back on after being turned off
To use device tunnel connections, such as IKEv2, Enable this setting.
Authentication method: Select how you want users to authenticate to the VPN server. Your options:
Username and password: Require users to enter their domain username and password to authenticate, such as
user@contoso.com, orcontosouser.Certificates: Select an existing user client certificate profile to authenticate the user. This option provides enhanced features, such as zero-touch experience, on-demand VPN, and per-app VPN.
To create certificate profiles in Intune, see Use certificates for authentication.
Derived credential: Use a certificate that's derived from a user's smart card. If no derived credential issuer is configured, Intune prompts you to add one. For more information, see Use derived credentials in Intune.
Machine certificates (IKEv2 only): Select an existing device client certificate profile to authenticate the device.
If you use device tunnel connections, you must select this option.
To create certificate profiles in Intune, see Use certificates for authentication.
EAP (IKEv2 only): Select an existing Extensible Authentication Protocol (EAP) client certificate profile to authenticate. Enter the authentication parameters in the EAP XML setting.
Remember credentials at each logon: Choose to cache the authentication credentials.
Custom XML: Enter any custom XML commands that configure the VPN connection.
EAP XML: Enter any EAP XML commands that configure the VPN connection. For more information, see EAP configuration.
Device tunnel (IKEv2 only): Enable connects the device to the VPN automatically without any user interaction or sign in. This setting applies to PCs joined to Azure Active Directory (AD).
To use this feature, the following are required:
- Connection type setting is set to IKEv2.
- Always On setting is set to Enable.
- Authentication method setting is set to Machine certificates.
Only assign one profile per device with Device Tunnel enabled.
IKE Security Association Parameters (IKEv2 only): These cryptography settings are used during IKE security association negotiations (also known as
main modeorphase 1) for IKEv2 connections. These settings must match the VPN server settings. If the settings don't match, the VPN profile won't connect.Encryption algorithm: Select the encryption algorithm used on the VPN server. For example, if your VPN server uses AES 128 bit, then select AES-128 from the list.
When set to Not configured, Intune doesn't change or update this setting.
Integrity check algorithm: Select the integrity algorithm used on the VPN server. For example, if your VPN server uses SHA1-96, then select SHA1-96 from the list.
When set to Not configured, Intune doesn't change or update this setting.
Diffie-Hellman group: Select the Diffie-Hellman computation group used on the VPN server. For example, if your VPN server uses Group2 (1024 bits), then select 2 from the list.
When set to Not configured, Intune doesn't change or update this setting.
Child Security Association Parameters (IKEv2 only): These cryptography settings are used during child security association negotiations (also known as
quick modeorphase 2) for IKEv2 connections. These settings must match the VPN server settings. If the settings don't match, the VPN profile won't connect.Cipher transform algorithm: Select the algorithm used on the VPN server. For example, if your VPN server uses AES-CBC 128 bit, then select CBC-AES-128 from the list.
When set to Not configured, Intune doesn't change or update this setting.
Authentication transform algorithm: Select the algorithm used on the VPN server. For example, if your VPN server uses AES-GCM 128 bit, then select GCM-AES-128 from the list.
When set to Not configured, Intune doesn't change or update this setting.
Perfect forward secrecy (PFS) group: Select the Diffie-Hellman computation group used for perfect forward secrecy (PFS) on the VPN server. For example, if your VPN server uses Group2 (1024 bits), then select 2 from the list.
When set to Not configured, Intune doesn't change or update this setting.
Pulse Secure example
F5 Edge Client example
SonicWALL Mobile Connect example
Login group or domain: This property can't be set in the VPN profile. Instead, Mobile Connect parses this value when the user name and domain are entered in the username@domain or DOMAINusername formats.
Example:
CheckPoint Mobile VPN example
Writing custom XML
For more information about writing custom XML commands, see each manufacturer's VPN documentation.
For more information about creating custom EAP XML, see EAP configuration.
Apps and Traffic Rules
Associate WIP or apps with this VPN: Enable this setting if you only want some apps to use the VPN connection. Your options:
- Associate a WIP with this connection: Enter a WIP domain for this connection
- Associate apps with this connection: You can Restrict VPN connection to these apps, and then add Associated Apps. The apps you enter automatically use the VPN connection. The type of app determines the app identifier. For a universal app, enter the package family name. For a desktop app, enter the file path of the app.
Important
We recommend that you secure all app lists created for per-app VPNs. If an unauthorized user changes this list, and you import it into the per-app VPN app list, then you potentially authorize VPN access to apps that shouldn't have access. One way you can secure app lists is using an access control list (ACL).
Network traffic rules for this VPN connection: Select the protocols, and the local & remote port and address ranges, are enabled for the VPN connection. If you don't create a network traffic rule, then all protocols, ports, and address ranges are enabled. After you create a rule, the VPN connection uses only the protocols, ports, and address ranges that you enter in that rule.
Conditional Access
Conditional Access for this VPN connection: Enables device compliance flow from the client. When enabled, the VPN client communicates with Azure Active Directory (AD) to get a certificate to use for authentication. The VPN should be set up to use certificate authentication, and the VPN server must trust the server returned by Azure AD.
Single sign-on (SSO) with alternate certificate: For device compliance, use a certificate different from the VPN authentication certificate for Kerberos authentication. Enter the certificate with the following settings:
- Name: Name for extended key usage (EKU)
- Object Identifier: Object identifier for EKU
- Issuer hash: Thumbprint for SSO certificate
DeployAnyConnect - Cisco
DNS Settings
DNS suffix search list: In DNS suffixes, enter a DNS suffix, and Add. You can add many suffixes.
When using DNS suffixes, you can search for a network resource using its short name, instead of the fully qualified domain name (FQDN). When searching using the short name, the suffix is automatically determined by the DNS server. For example,
utah.contoso.comis in the DNS suffix list. You pingDEV-comp. In this scenario, it resolves toDEV-comp.utah.contoso.com.DNS suffixes are resolved in the order listed, and the order can be changed. For example,
colorado.contoso.comandutah.contoso.comare in the DNS suffix list, and both have a resource calledDEV-comp. Sincecolorado.contoso.comis first in the list, it resolves asDEV-comp.colorado.contoso.com.To change the order, select the dots to the left of the DNS suffix, and then drag the suffix to the top:
Name Resolution Policy table (NRPT) rules: Name Resolution Policy table (NRPT) rules define how DNS resolves names when connected to the VPN. After the VPN connection is established, you choose which DNS servers the VPN connection uses.
You can add rules to the table that include the domain, DNS server, proxy, and other details to resolve the domain you enter. The VPN connection uses these rules when users connect to the domains you enter.
Select Add to add a new rule. For each server, enter:
- Domain: Enter the fully qualified domain name (FQDN) or a DNS suffix to apply the rule. You can also enter a period (.) at the beginning for a DNS suffix. For example, enter
contoso.comor.allcontososubdomains.com. - DNS servers: Enter the IP address or DNS server that resolves the domain. For example, enter
10.0.0.3orvpn.contoso.com. - Proxy: Enter the web proxy server that resolves the domain. For example, enter
http://proxy.com. - Automatically connect: When Enabled, the device automatically connects to the VPN when a device connects to a domain you enter, such as
contoso.com. When Not configured (default), the device doesn't automatically connect to the VPN - Persistent: When set to Enabled, the rule stays in the Name Resolution Policy table (NRPT) until the rule is manually removed from the device, even after the VPN disconnects. When set to Not configured (default), NRPT rules in the VPN profile are removed from the device when the VPN disconnects.
- Domain: Enter the fully qualified domain name (FQDN) or a DNS suffix to apply the rule. You can also enter a period (.) at the beginning for a DNS suffix. For example, enter
Proxy
- Automatic configuration script: Use a file to configure the proxy server. Enter the proxy server URL that includes the configuration file. For example, enter
http://proxy.contoso.com/pac. - Address: Enter the IP address or fully qualified host name of the proxy server. For example, enter
10.0.0.3orvpn.contoso.com. - Port number: Enter the port number used by your proxy server. For example, enter
8080. - Bypass proxy for local addresses: This setting applies if your VPN server requires a proxy server for the connection. If you don't want to use a proxy server for local addresses, then choose Enable.
Split Tunneling
- Split tunneling: Enable or Disable to let devices decide which connection to use depending on the traffic. For example, a user in a hotel uses the VPN connection to access work files, but uses the hotel's standard network for regular web browsing.
- Split tunneling routes for this VPN connection: Add optional routes for third-party VPN providers. Enter a destination prefix, and a prefix size for each connection.
Cisco Anyconnect Intune Windows 10 Free
Trusted Network Detection
Trusted network DNS suffixes: When users are already connected to a trusted network, you can prevent devices from automatically connecting to other VPN connections.
Configure ASA AnyConnect VPN With Microsoft Azure MFA ... - Cisco
In DNS suffixes, enter a DNS suffix that you want to trust, such as contoso.com, and select Add. You can add as many suffixes as you want.
If a user is connected to a DNS suffix in the list, then the user won't automatically connect to another VPN connection. The user continues to use the trusted list of DNS suffixes you enter. The trusted network is still used, even if any autotriggers are set.
For example, if the user is already connected to a trusted DNS suffix, then the following autotriggers are ignored. Specifically, the DNS suffixes in the list cancel all other connection autotriggers, including:
- Always on
- App-based trigger
- DNS autotrigger
Cisco Anyconnect Intune Windows
Next steps
The profile is created, but may not be doing anything yet. Be sure to assign the profile, and monitor its status.
Intune Vpn Profile Cisco Anyconnect Windows 10
Configure VPN settings on Android, iOS/iPadOS, and macOS devices.
