Provided you didn't override it using.bashprofile, bash runs.profile when started as a login shell. And SSH starts bash as a login shell. – muru Mar 7 '16 at 22:44 It is correct that /.profile is not read if /.bashprofile exists.
About the original question: change the shell opened by a SSH session, I don't think that it is configurable. You can change the shell used by the user on the system (chsh, or edit /etc/passwd), or even change the default shell of the machine, but not the SSH shell (I think SSH just opens a regular session with the user's parameters, including shell configuration). Connect to your device In order to connect to your device, you need to first get the IP address of the device. After booting your Windows IoT. Now launch PuTTY and enter the IP address in the Host Name text box and make sure the SSH radio button is selected. If you're connecting to your. The Secure Shell extension works with non-Google HTTP-to-SSH proxies via proxy hooks, and third-party application nassh-relay can use those hooks to enable the Secure Shell extension to establish an SSH connection over XMLHttpRequest or WebSocket transport.
Web-based SSH makes it possible to access Secure Shell (SSH) servers through standard web browsers. Respective clients are typically based on JavaScript/Ajax or JavaScript/WebSockets, and, if they work together with an Ajax/WebSocket-to-SSH proxy, can be used to access SSH servers from behind a firewall or proxy that allows HTTP traffic but does not allow SSH traffic.
Technology[edit]
Web-based SSH clients basically consist of the following parts:
- Client-side: Typically JavaScript and dynamic HTML pages are used to capture keystrokes, transmit messages to/from the server and display the results in the user's web browser.
- Server-side/Web application: Incoming requests are processed on the web application server. Keyboard events are forwarded to a secure shell client communicating with the connected SSH server. Terminal output is either passed to the client where it is converted into HTML via JavaScript or it is translated into HTML by the server before it is transmitted to the client.
Client-side terminal emulation[edit]
Web-based SSH servers that utilize client-side terminal emulation typically transmit the raw terminal output from the SSH server directly to the client. This has the advantage of offloading the process of translating terminal output into HTML on to the client. The disadvantage of this method is that it is limited by the capabilities of JavaScript and it will use up a non-trivial amount of the client's CPU and memory to process the incoming character stream. It also relies on the client to keep track of the terminal state and respond to escape sequences.
Client-side terminal emulator example: vt100.js[1]
Server-side terminal emulation[edit]
Web-based SSH servers that utilize server-side terminal emulation typically keep track of the terminal screen and state in memory and convert it to HTML either when a screen update occurs or when the client expressly requests an update. The advantage of this method is that the state of the terminal remains persistent even if the user connects to their existing session(s) from a different web browser. It also enables the server to act upon terminal output even if the user is disconnected.[2] The disadvantage of this method is that it uses up more CPU and memory on the server.
Server-side terminal emulator example: terminal.py[3]
Advantages[edit]
The main advantages of web-based SSH can be summarized as follows:
- Accessibility: Web-based SSH as described in this article requires no local installation of client software. It is thus possible to access SSH servers through a web browser from anywhere. As communication is based on HTTP or HTTPS it is also possible to access SSH servers from behind a firewall or proxy that restricts Internet access to only ports 80 (HTTP) or 443 (HTTPS).
- Anonymous Access: As SSH access is tunneled through an intermediary web application server it is this server which actually communicates with the SSH server. This means that the SSH server will only be aware of the IP address of the web application server, keeping the actual client's IP address hidden.
- Auditability: Because all communication between the client and the SSH server must pass through the web application server this communication can be logged. This prevents a malicious client from deleting logs of their activities. The situation is exactly the same as with traditional SSH server.
- Resuming Sessions: Some web-based SSH implementations allow the user to resume their SSH sessions after being disconnected. This is not possible with a traditional SSH client.
- Embeddable: Web-based SSH implementations can be embedded into any web page allowing them to be integrated into other web-based applications.
- Unique Features: Many web-based SSH tools have unique features such as the ability to share terminals with other users, can display images within terminals, and other useful capabilities.
Important issues[edit]
The following issues have to be considered and are important when using a web-based SSH client:
- Security: It is important to make sure that HTTPS is used when communicating with the web application server. Otherwise all data being sent would be readable by use of simple packet sniffers which could reveal sensitive information.
- Trust: The data being sent to the web application server is decrypted there. This is necessary in order to forward the issued commands to the actual SSH server. Even though the operators of web-based SSH solutions usually don't log sensitive data the data is theoretically available to them in plain form. It is unlikely that this will cause a security issue when the web application server and the SSH server are run on the same server or are controlled by the same entity.
- Tunneling: Unlike most traditional, application based SSH clients, web-based SSH clients are unable to tunnel ('forward') TCP traffic. For example, running an X session over a web-based SSH session is not possible. However, the lack of ability is caused by implementation issues, and not inherent in some way.[4]
Free and open source examples[edit]
- Google's Secure Shell extension for Chrome and Chromium[5] pairs the JavaScript hterm terminal emulator with OpenSSH client code running on Native Client.[6] The Secure Shell extension works with non-Google HTTP-to-SSH proxies via proxy hooks, and third-party application nassh-relay[7] can use those hooks to enable the Secure Shell extension to establish an SSH connection over XMLHttpRequest or WebSocket transport.
- shellinabox[8] operates as a stand-alone service or in conjunction with nginx to provide HTTPS access to a login shell, and is packaged for Debian and RedHat -derived Linux distributions.
- webssh[9] is a similar solution written in Python.
- Bastillion[10] is a self hosted, web-based bastion host with auditing and key management capabilities. Users connect to a centralized server over HTTPS and SSH connections are proxied through a secure WebSocket transport.
- FireSSH is a browser plug-in that works on Firefox ESR and Waterfox.
References[edit]
- ^http://code.google.com/p/shellinabox/source/browse/demo/vt100.js
- ^The expect function from Gate One's termio.py module can act upon terminal output even if the user is disconnected.
- ^https://liftoff.github.io/GateOne/Developer/terminal.html
- ^jcterm claims to be able to handle port forwarding, such as X11 forwarding
- ^https://chrome.google.com/webstore/detail/pnhechapfaindjhompbnflcldabbghjo
- ^Chromium Secure Shell FAQ
- ^nassh-relay GitHub repository
- ^https://github.com/shellinabox/shellinabox
- ^https://pypi.org/project/webssh/
- ^Bastillion - Web-Based SSH Access and Key Management

Secure Shell (SSH) allows you to remotely administer and configure your Windows IoT Core device
Using the Windows 10 OpenSSH client
Important
The Windows OpenSSH client requires that your SSH client host OS is Windows 10 version 1803(17134). Also, the Windows 10 IoT Core device must be running RS5 Windows Insider Preview release 17723 or greater.
The OpenSSH Client was added to Windows 10 in 1803 (build 17134) as an optional feature. To install the client, you can search for Manage Optional Features in Windows 10 settings. If the OpenSSH Client is not listed in the list of installed features, then choose Add a feature.

Next select OpenSSH Client in the list and click Install.
To login with a username and password use the following command:
Where host is either the IP address of the Windows IoT Core device or the device name.
The first time you connect you see a message like the following:
Type yes and press enter.
If you need to login as DefaultAccount rather than as administrator, you will need to generate a key and use the key to login. From the desktop that you intend to connect to your IoT Device from, open a PowerShell window and change to your personal data folder (e.g cd ~)
Register the key with ssh-agent (optional, for single sign-on experience). Note that ssh-add must be performed from a folder that is ACL'd to you as the signed-in user (BuiltinAdministrators and the NT_AUTHORITYSystem user are also ok). By default cd ~ from PowerShell should be sufficient as shown below.
Tip
If you receive a message that the ssh-agent service is disabled you can enable it with sc.exe config ssh-agent start=auto
To enable single sign, append the public key to the Windows IoT Core device authorized_keys file. Or if you only have one key you copy the public key file to the remote authorized_keys file.
If the key is not registered with ssh-agent, it must be specified on the command line to login:
If the private key is registered with ssh-agent, then you only need to specify DefaultAccount@host:
Ssh Secure Shell Download
The first time you connect you see a message like the following:
Type yes and press enter.
You should now be connected as DefaultAccount
To use single sign-on with the administrator account, append your public key to c:dataProgramDatasshadministrators_authorized_keys on the Windows IoT Core device.
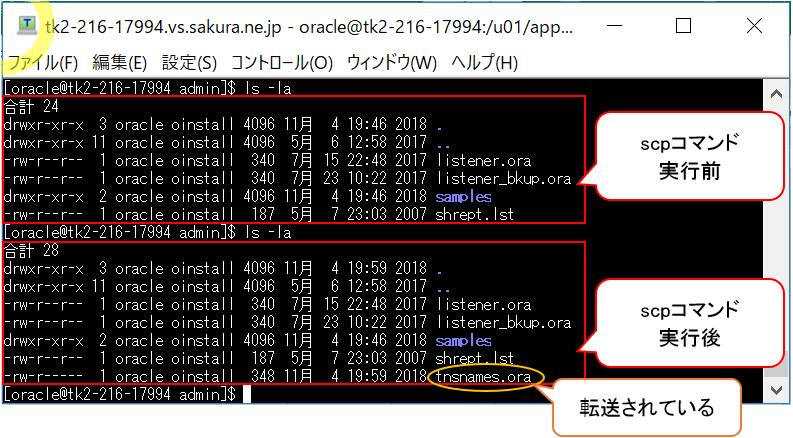
You will also need to set the ACL for administrators_authorized_keys to match the ACL of ssh_host_dsa_key in the same directory.
To set the ACL using PowerShell
Note
If you see a REMOTE HOST IDENTIFICATION CHANGED message after making changes to the Windows 10 IoT Core device, then edit C:Users<username>.sshknown_hosts and remove the host that has changed.
See also: Win32-OpenSSH
Using PuTTY
Download an SSH client
In order to connect to your device using SSH, you'll first need to download an SSH client, such as PuTTY.
Connect to your device
In order to connect to your device, you need to first get the IP address of the device. After booting your Windows IoT Core device, an IP address will be shown on the screen attached to the device:
Now launch PuTTY and enter the IP address in the
Host Nametext box and make sure theSSHradio button is selected. Then clickOpen.If you're connecting to your device for the first time from your computer, you may see the following security alert. Just click
Yesto continue.If the connection was successful, you should see
login as:on the screen, prompting you to login.
EnterAdministratorand press enter. Then enter the default passwordp@ssw0rdas the password and press enter.If you were able to login successfully, you should see something like this:
Golang Ssh Shell
Update account password
It is highly recommended that you update the default password for the Administrator account.
To do this, enter the following command in the PuTTY console, replacing [new password] with a strong password:
Configure your Windows IoT Core device
To be able to deploy applications from Visual Studio 2017, you will need to make sure the Visual Studio Remote Debugger is running on your Windows IoT Core device. The remote debugger should launch automatically at machine boot time. To double check, use the tlist command to list all the running processes from PowerShell. There should be two instances of msvsmon.exe running on the device.
It is possible for the Visual Studio Remote Debugger to time out after long periods of inactivity. If Visual Studio cannot connect to your Windows IoT Core device, try rebooting the device.
If you want, you can also rename your device. To change the 'computer name', use the
setcomputernameutility:
You will need to reboot the device for the change to take effect. You can use the shutdown command as follows:
Commonly used utilities
Ssh Shell Client
See the Command Line Utils page for a list of commands and utilities you can use with SSH.
